You're happily using your Raspberry Pi. Perhaps it's a game center, or a media center. Hopefully you've tried a few other uses for this incredibly versatile little computer. But is it secure?
It's relatively simple to change passwords and keep your Raspberry Pi secure. But installing software and using the Pi in a particular way can weaken any steps you might have taken. Here are five ways that online threats could ruin your Raspberry Pi experience, from retro gaming to hosting a website.
Basic Raspberry Pi Security
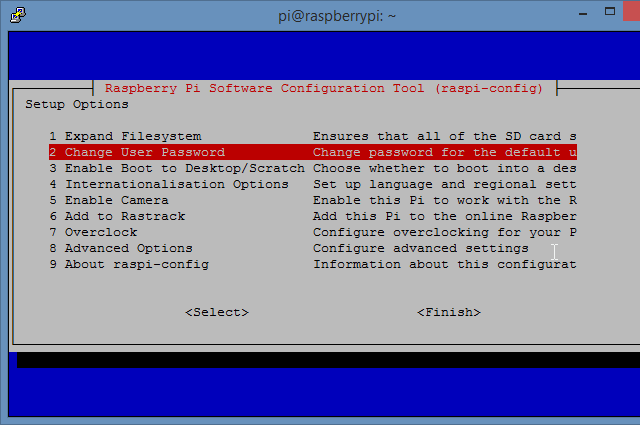
So many Raspberry Pi users forget the basics of computer security. Are you still using the default Raspbian username and password? If not, how long did it take you to change it?
It's particularly frustrating as the Pi is simple to secure. Passwords and usernames can be changed, firewalls can be installed, and you can even lock the Raspberry Pi away because it's small enough! Just as important is the risk of putting your Pi on the network unnecessarily.
You might have taken security precautions. But installing new software, or using the computer in a new way, can undo any steps you've taken to secure your Raspberry Pi.
1. Kodi as a Threat
One of the most popular uses of the Raspberry Pi -- despite its purpose as an educational device -- is to run the Kodi media center. Several versions of Kodi are available for the Pi, and the minicomputer offers an experience comparable with Kodi on desktops, consoles, and dedicated set-top boxes.
As a result, threats to Kodi are also comparable. Among the risks are man-in-the-middle attacks, but addons harboring malware are a particular concern. If you're not running an antivirus solution like ClamAV, there's a potential risk here.
But Kodi also attracts ISP tracking (especially if you're using it illegally), and maintains a local database of every single video you've watched. And then there's outdated addons, and addons that might be bought or hijacked by malicious parties.
The smart solution is to avoid Kodi on your Raspberry Pi. If you're determined to use it, however, stick to the official addons.
2. Your Raspberry Pi Web Server: Is It Secure?
One popular use for the Raspberry Pi is as a web server. In most cases, the software running the server, a local firewall, and your router, should be enough. But the software you're using to host the website might be prone to intrusion.
A popular option for the Raspberry Pi is WordPress. Unfortunately, the widely-used blog and website software is subject to regular probing from hackers. While regular updates to the WordPress software are released to help deal with this, it's worth applying some basic security steps. Once this is done, consider one or two security-based plugins. WordFence is a good example, but just as useful might be a throttling plugin. This will help to prevent DDOS attacks, which can be used to gain entry to your site.
3. Is It Safe to Use Your Raspberry Pi as a Game Server?
There is a lot you can do with games on the Raspberry Pi. You might write them, for instance, or learn the basics using tools like Scratch. It's also possible to run ported versions of old PC games on the lowly Raspberry Pi.
However, in addition to using the Raspberry Pi as a web server, it can also be configured for use as a game server. If you know and trust the users of your online games, you'll probably be okay. But this doesn't rule out the uncomfortable fact that vulnerabilities in game servers can be exploited -- whatever the platform.
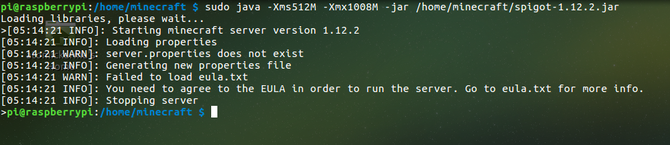
If you're using a Raspberry Pi to host Minecraft or some other multiplayer game, take steps to ensure it is regularly updated. Using Java? Apply updates regularly!
4. Attacks via Connected Devices
What hardware do you connect your Raspberry Pi to? You've no doubt got a wireless dongle, but what about third party hardware that connects to the GPIO? Or devices you connect to via USB cable? What is the risk from cables you've made yourself for custom projects?
In most cases anything you connect to your Raspberry Pi will typically be dumb. But there are certain cases where devices you attempt to control with your Pi can open a door to the computer, and your home network.
And then there's the Internet of Things and home automation projects, or even a full-scale smart home integration with OpenHAB. Custom-coded applications might fulfil a particular task, but do they (potentially) enable hackers to access your Raspberry Pi?
5. The Danger of Retro Gaming ROMs
Beyond the Kodi-based media center, one of the most popular uses for a Raspberry Pi is as a retro gaming device. Five emulation suites are available for the Pi, which might then be fitted into an arcade-style case. Some fans have even built full-sized arcade cabinets for their tiny computers!
The risks from emulation are two-fold:
- With so many emulators available (over 40 in some cases) there is plenty of scope for vulnerabilities to be introduced. For instance, RecalBox has introduced online play for some classic computer and console platforms that didn't support it.
- There is also a risk from ROMs. Video game ROMs are commonly found on dedicated websites (unless you've bought a rare, legal collection). These sites aren't immune to things like malvertising. They're also prone to compromised uploads of apparently genuine games.
Meanwhile, there's also the issue of legality. While the gaming ROMs themselves should only be used if you own the original game, the situation around the BIOS ROMs -- virtual versions of the operating system of each emulated platform -- cannot be fudged so easily. In short, you shouldn't be using them unless you've extracted the data from your own system.
Raspberry Pi's Third Party Vulnerabilties
We've already looked at the steps you can take to avoid security threats affecting your Raspberry Pi. It's important that you team this information up with the active threats to popular Pi projects. Vulnerabilities in retro gaming emulators and media centers don't have to be targeted at the Raspberry Pi to affect you. The same goes for web hosting and blogging software. As such, stay aware of the risks.
Do you use a Raspberry Pi for any of these purposes? Has your device experienced any attacks based on the vulnerabilities we've looked at? We'd love to hear about it, tell us what happened.
Image Credit: logoff/Depositphotos