If you've ever performed any network monitoring, you should be familiar with Nmap. It is a powerful port scanner that allows admins to locate weak points in their network.
You can investigate an entire network, view running services, and discover known vulnerabilities using a single nmap command. This guide showcases some useful ways of analyzing network services using nmap in Linux.
How to Scan Networks Using Nmap
Nmap can scan entire networks for available hosts and open ports. There are several scan methods to choose from. Aggressive scan types yield more information, but firewalls may flag them. Stealthy scans, on the other, are more suitable in real-world scenarios.
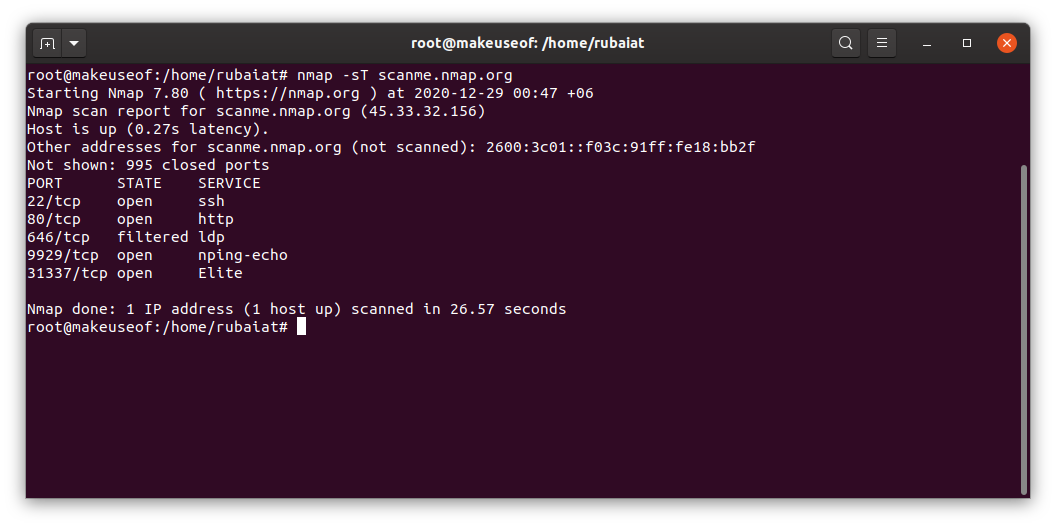
nmap -sT scanme.nmap.org
This is a TCP connect scan. These types of scans complete the three-way TCP handshake with the host. However, it also makes it easy for the host to block such scans. Plus, they also take longer to finish.
SYN scans, on the other hand, don't complete the entire three-way handshake. Thus, it's harder to block and faster than TCP connect scans.
>nmap -sS scanme.nmap.org
Since most of the web uses TCP, UDP scans are less frequent. However, you can use them to find DNS, SNMP, and DHCP services.
nmap -sU scanme.nmap.org
The SCTP INIT scan is another robust feature of nmap in Linux. However, not all devices use this protocol yet. So, the surveillance surface may be shorter. Regardless, these scans are fast, stealthy, and accurate.
nmap -sY scanme.nmap.org
How to Specify Hosts Using Nmap in Linux
Nmap allows admins to analyze networks in several methods. You can scan a single IP, a range of IPs, and selected IPs.
nmap -sS 192.168.1.1
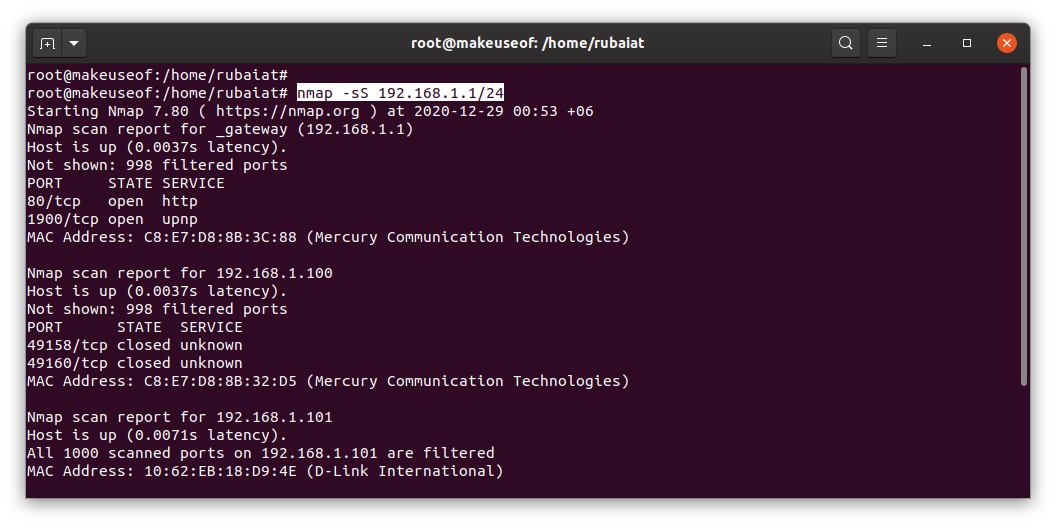
nmap -sS 192.168.1.1/24
nmap -sS 192.168.1.1 192.168.1.101 192.168.1.201
All of these nmap scans are performed on the local network. You can also scan remote networks the same way.
Make sure you have the required permissions if you don't want to land in legal challenges though. We recommend creating a Virtual Machine(VM) for testing these nmap commands. It's one of the more practical reasons for using a Virtual Machine.
How to Specify Ports in Nmap
Nmap scans for the most popular 1000 ports by default. However, they often take way more time and can trigger firewalls or intrusion detection systems. We can specify the remote ports to get around this issue.
nmap -sS -p 80,443 192.168.1.1
nmap -sS -p 21-25,80,139,8080 192.168.1.1
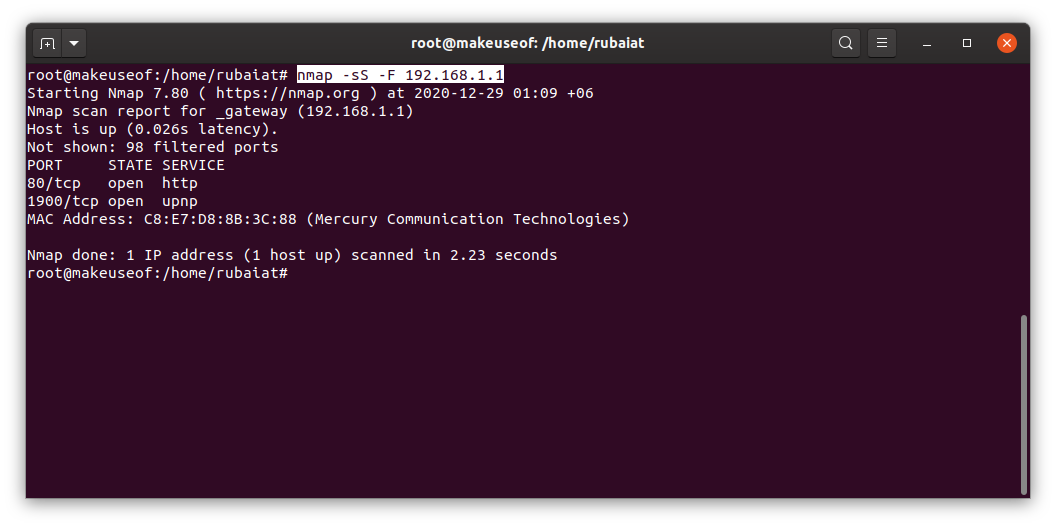
You can add as many ports you want using the -p option. The -F option selects the fast mode, which basically scans fewer ports than the default scan.
nmap -sS -F 192.168.1.1
The --top-ports option allows admins to specify the most popular ports. This can be helpful for large-scale reconnaissance.
nmap -sS --top-ports 10 192.168.1.1
How to Detect Services and Version Information
Nmap is great at finding services and their version information. These data are pretty accurate in most cases. You can add version detection to your nmap scan by adding the -sV option.
nmap -sS -sV -p 80,443 192.168.1.1
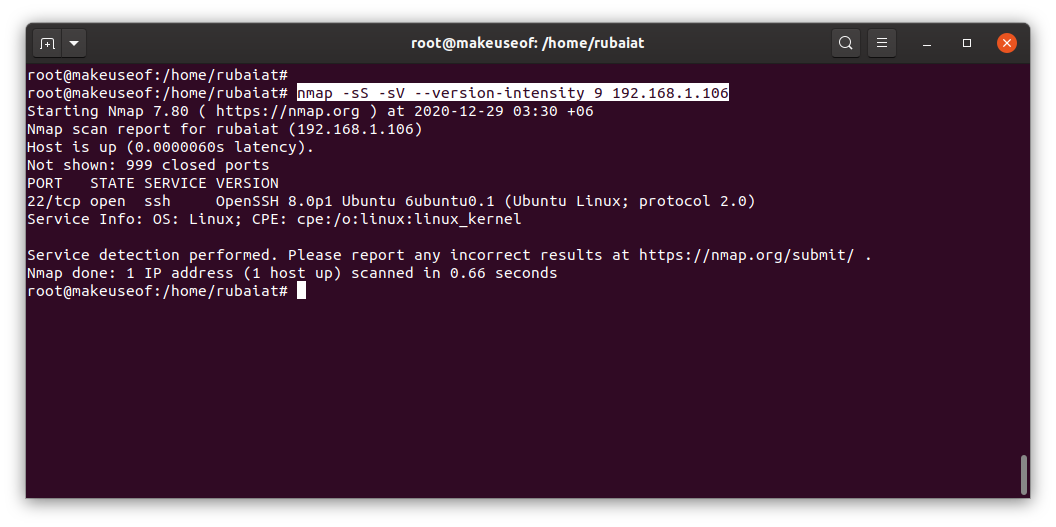
Nmap utilizes several techniques to grab version information. You can control the operation using the --version-intensity option. The greater the intensity, the more accurate the result. However, they also take significantly more time.
nmap -sS -sV --version-intensity 9 192.168.1.1
You can also use nmap to detect OS versions. This is very helpful since you discover the outdated services right away.
nmap -sS -O -p 80,443 192.168.1.1
The --osscan-guess option may provide a little bit more information in some scenarios. But, it's much more intrusive.
nmap -sS --osscan-guess 192.168.1.1
You can also use the -A option for enabling version and OS detection alongside traceroute.
nmap -sS -A -p 80,443 192.168.1.1
How to Use Nmap Scripts in Linux?
Nmap scripts combine power and flexibility. Admins can choose from a variety of community-driven NSE scripts or create custom ones themselves. Nmap categorizes the default scripts for making them easier to use.
nmap --script=version 192.168.1.1
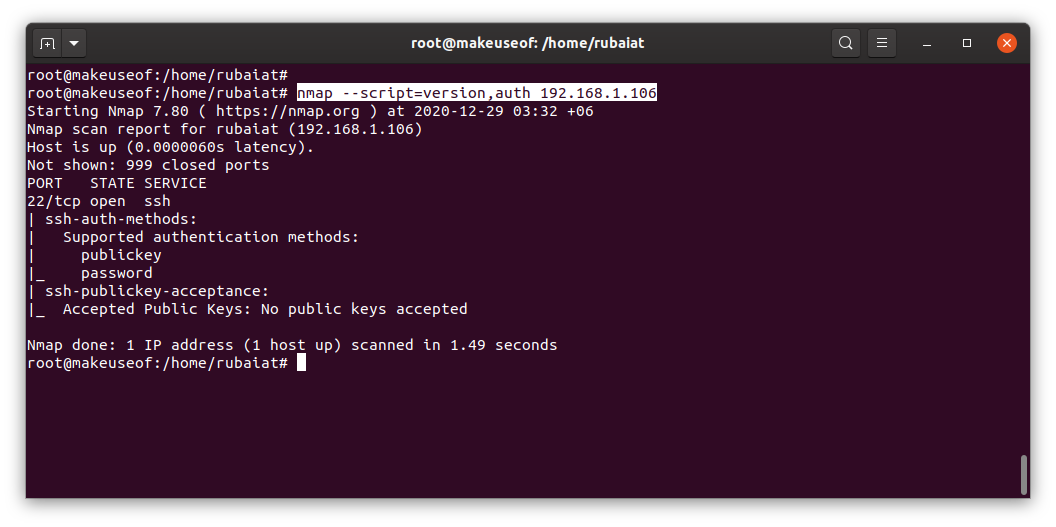
Nmap scripts are written in Lua and stored at /usr/share/nmap/nselib/. Some other interesting NSE scripts include auth, vulns, exploit, and brute. You can use multiple scripts using a comma-separated list.
nmap --script=version,auth 192.168.1.1
Adding spaces between the commas will break the scan. Make sure to avoid them. You can also specify related scripts using bash-style wildcards.
nmap --script=http* 192.168.1.1
You can always learn more about a nmap script using the --script-help option.
nmap --script-help "discovery"
How to Control Scan Timing for Nmap in Linux
Nmap provides excellent performance out of the box. However, you can also tweak the timing for meeting your scan objectives. The -T option allows us to set a timing template between zero to five. Higher values specify faster scans.
nmap -sS -T 2 --top-ports 10 192.168.1.1
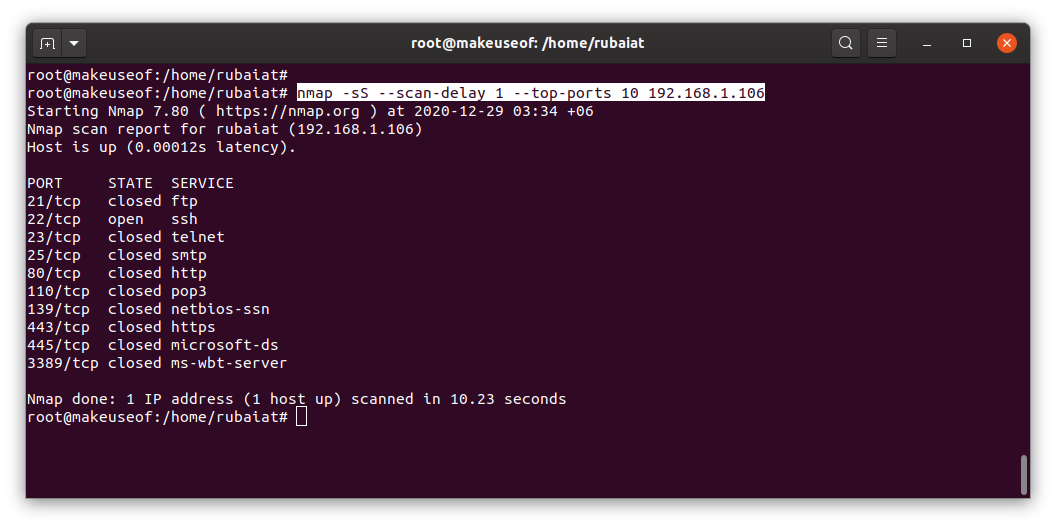
Users can also specify a delay between each probe sent by nmap. You can use this for evading firewalls. The delay is specified in seconds.
nmap -sS --scan-delay 1 --top-ports 10 192.168.1.1
How to Evade Firewalls for Nmap Scans?
Technology has come a long way since Nmap was released. Most firewalls today can detect port sweeps and block the source address altogether. Nmap offers several methods to evade firewalls and IDS's.
nmap -sS -D 192.168.1.111 --top-ports 10 192.168.1.1
The -D option sets a decoy IP address. This doesn't mask your IP, though. Instead, it makes it look like multiple hosts are sending the same scan probes.
nmap -sS -e wlp2s0 -S 192.168.1.111 --top-ports 10 192.168.1.1
You can use the -S option to spoof your IP address. You will need to use the -e option for spoofing your source address, though. It takes an interface name as the argument. You can also spoof the MAC address.
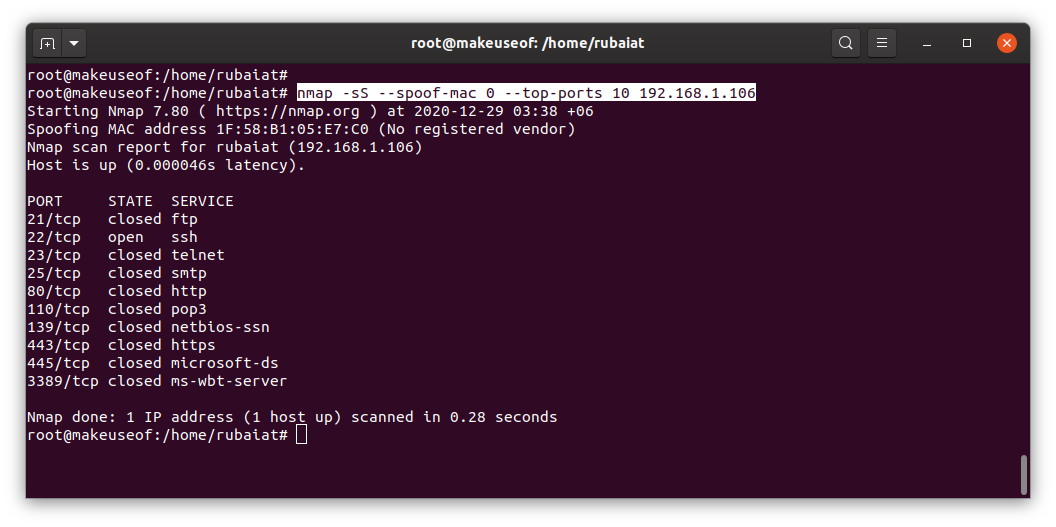
nmap -sS --spoof-mac 0 --top-ports 10 192.168.1.1
Specifying a zero value for --spoof-mac tells nmap to generate a random MAC for that session. You can always use custom addresses.
How to Manage the Nmap Output
Nmap offers several ways of handling the scan output. You can save the result of a scan session to specific files.
nmap -sS -p 80,443 -oN scan-output 192.168.1.1
Many admins like to save the output as XML. This makes it easier to parse.
nmap -sS -p 80,443 -oX scan-output 192.168.1.1
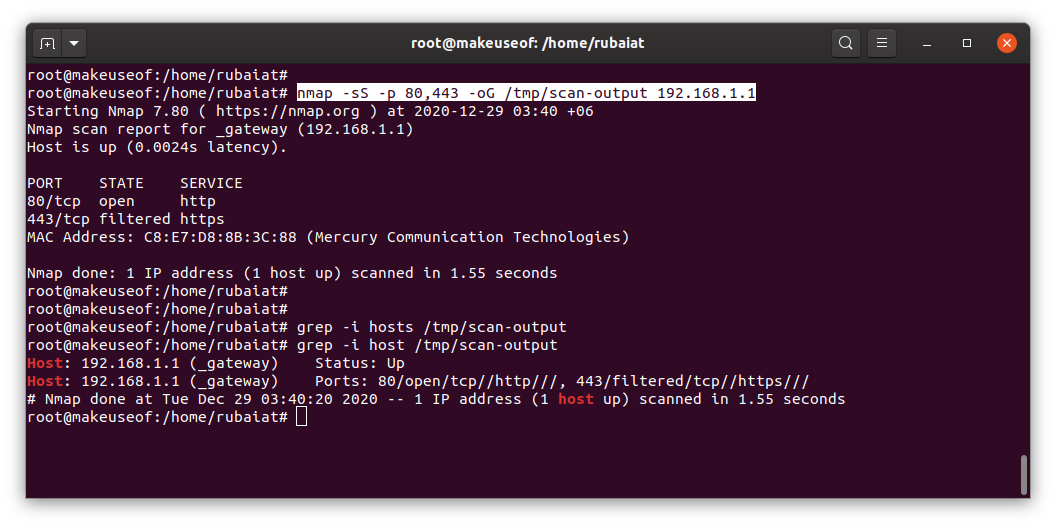
I personally like to save the output in a grepable file. This makes parsing the data easier using popular Unix tools like grep, cut, and awk.
nmap -sS -p 80,443 -oG scan-output 192.168.1.1
Analyze Network Services Using Nmap
Nmap makes network discovery effortless. You can choose from a plethora of scan techniques to meet different objectives. Plus, a collection of powerful NSE scripts makes finding vulnerable services much easier.