Wireshark is the leading network protocol analyzer used by security professionals all over the world. It allows you to detect anomalies in computer networks and find the underlying causes. We will demonstrate how to use Wireshark in the following sections.
So how does it work? And how do you actually use Wireshark to capture data packets?
How Does Wireshark Work?
Wireshark's robust feature set has made it one of the best tools to troubleshoot network issues. Many people use Wireshark, including network admins, security auditors, malware analysts, and even attackers.
It allows you to perform deep inspections of live or stored network packets. As you begin to use Wireshark, you'll be fascinated by the amount of information it can offer. However, too much information often makes it hard to stay on track.
Luckily, we can mitigate this via Wireshark's advanced filtering capabilities. We'll discuss them in detail later. The workflow consists of capturing network packets and filtering out the required information.
How to Use Wireshark for Packet Capturing
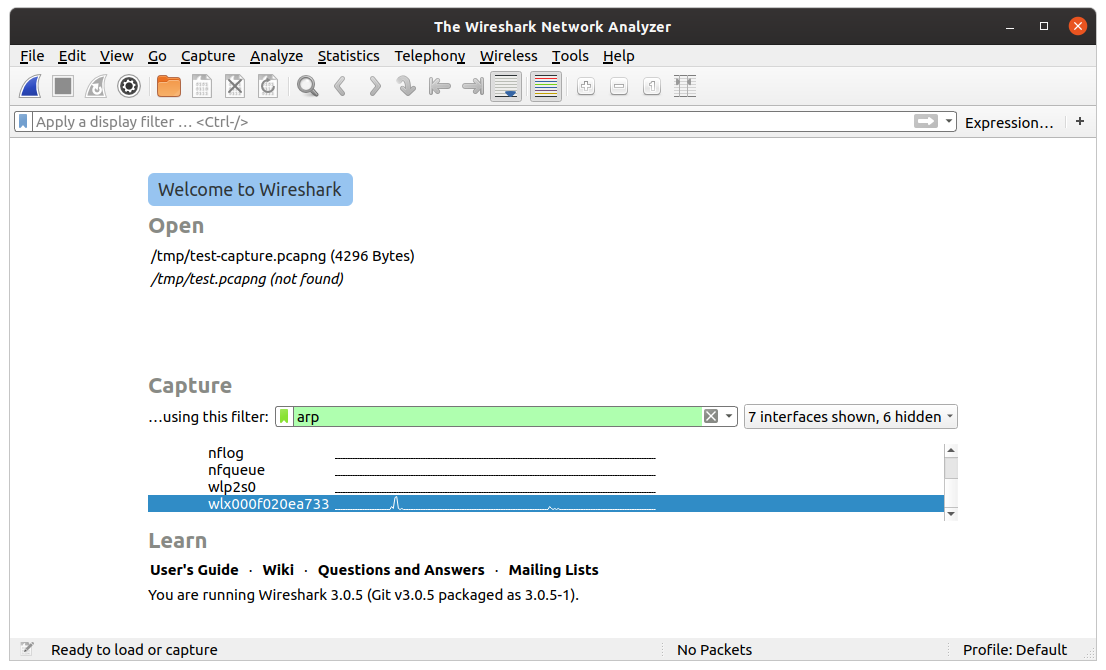
Once you start Wireshark, it will display the network interfaces connected to your system. You should notice curves representing network communication beside each interface.
Now, you need to choose a specific interface before you can start capturing packets. To do this, select the interface name and click on the blue shark fin icon. You can also do this by double-clicking on the interface name.
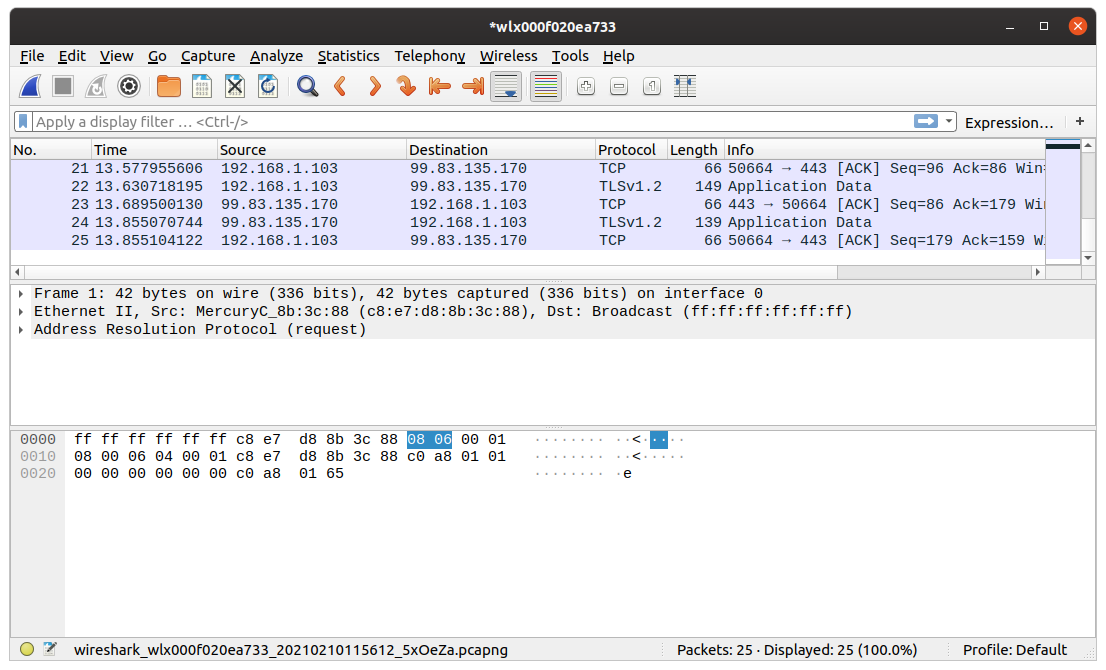
Wireshark will start capturing the incoming and outgoing packets for the selected interface. Click on the red pause icon to halt the capture. You should see a list of network packets taken during this process.
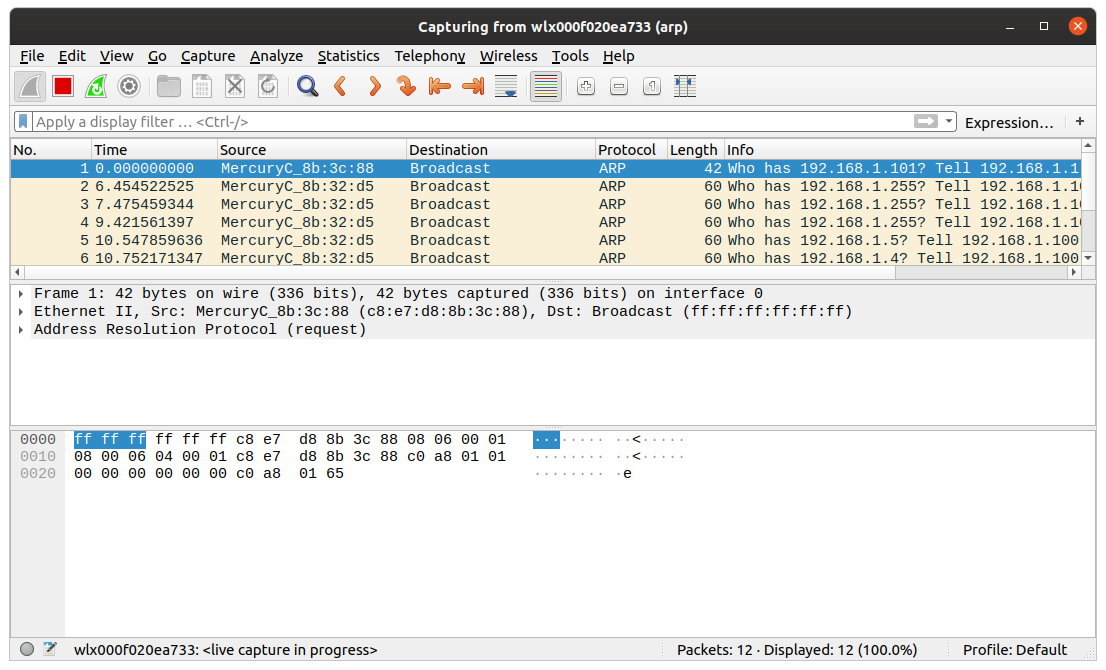
Wireshark will display the source and destination for each packet alongside the protocol. However, most of the time, you will be interested in the contents of the information field.
You can inspect individual packets by clicking on them. This way, you can view the entire packet data.
How to Save Captured Packets in Wireshark
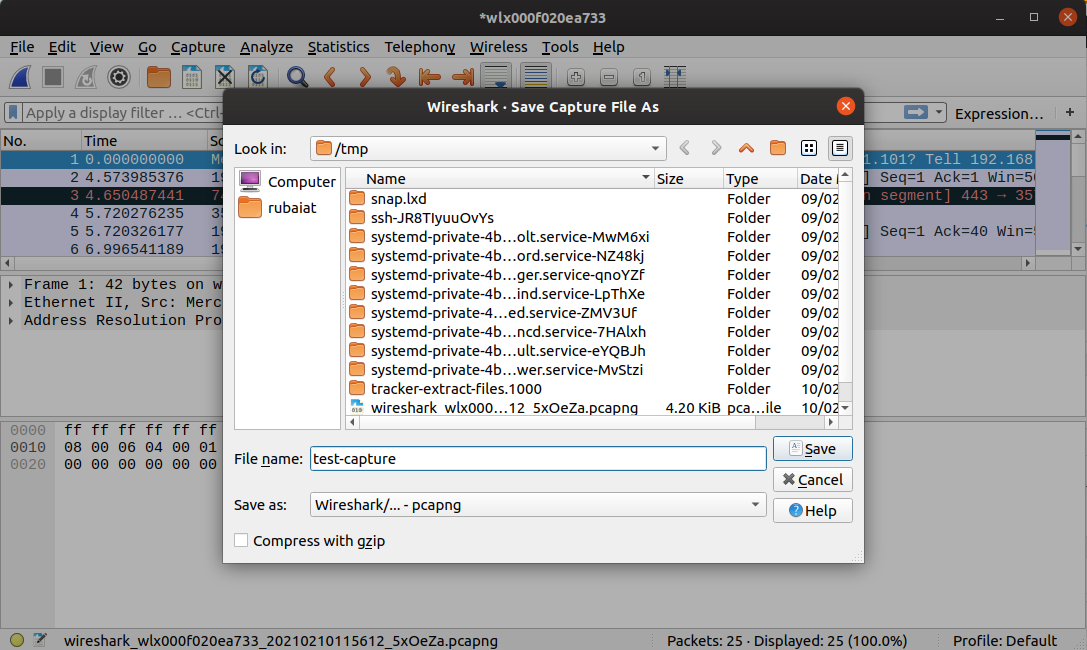
Since Wireshark captures a lot of traffic, sometimes you may want to save them for later inspection. Luckily, saving captured packets with Wireshark is effortless.
To save packets, stop the active session. Then click on the file icon located in the top menu. You can also use Ctrl+S to do this.
Wireshark can save packets in several formats, including pcapng, pcap, and dmp. You can also save captured packets in a format that other network analysis tools can later use.
How to Analyze Captured Packets
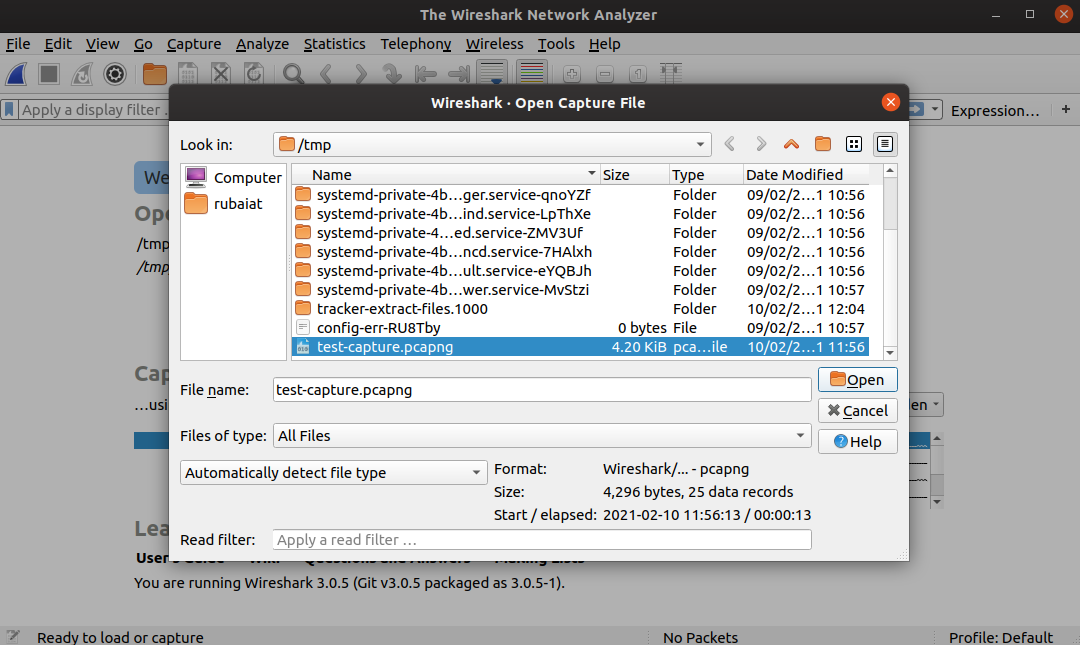
You can analyze previously captured packets by opening the capture file. Once in the main window, click File > Open and then select the relevant saved file.
You can also use Ctrl+O to do this quickly. Once you've analyzed the packets, quit the inspection window by going to File > Close.
How to Use Wireshark Filters
Wireshark offers a plethora of robust filtering capabilities. Filters are of two types—display filters, and capture filters.
Using Wireshark Display Filters
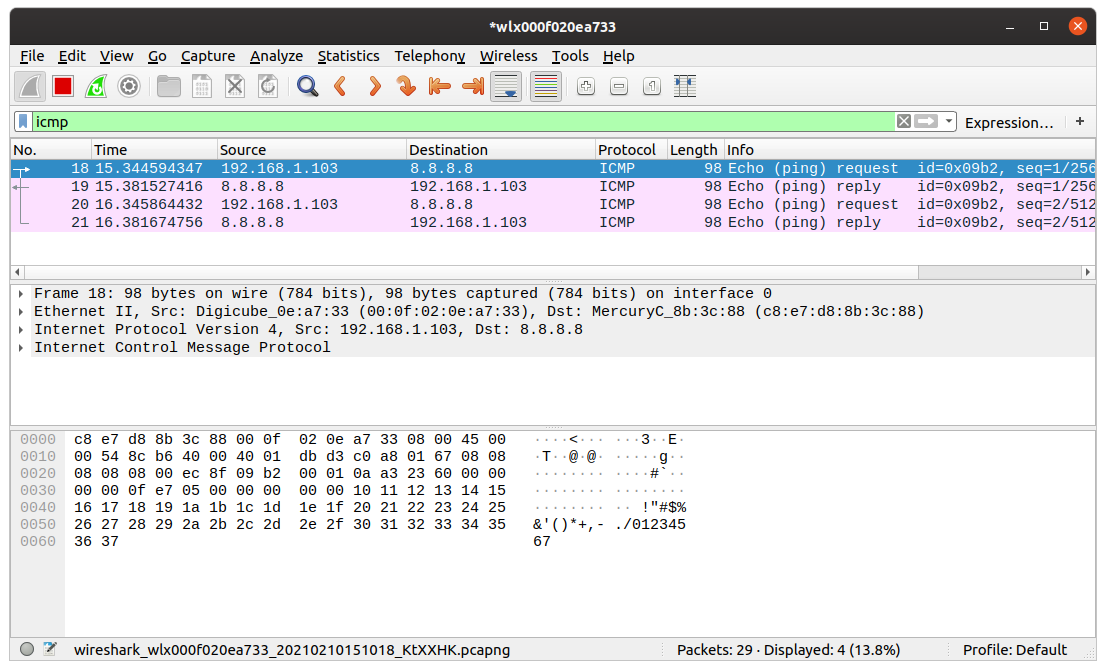
Display filters are used for viewing specific packets from all the captured packets. For example, we can use the display filter icmp to view all ICMP data packets.
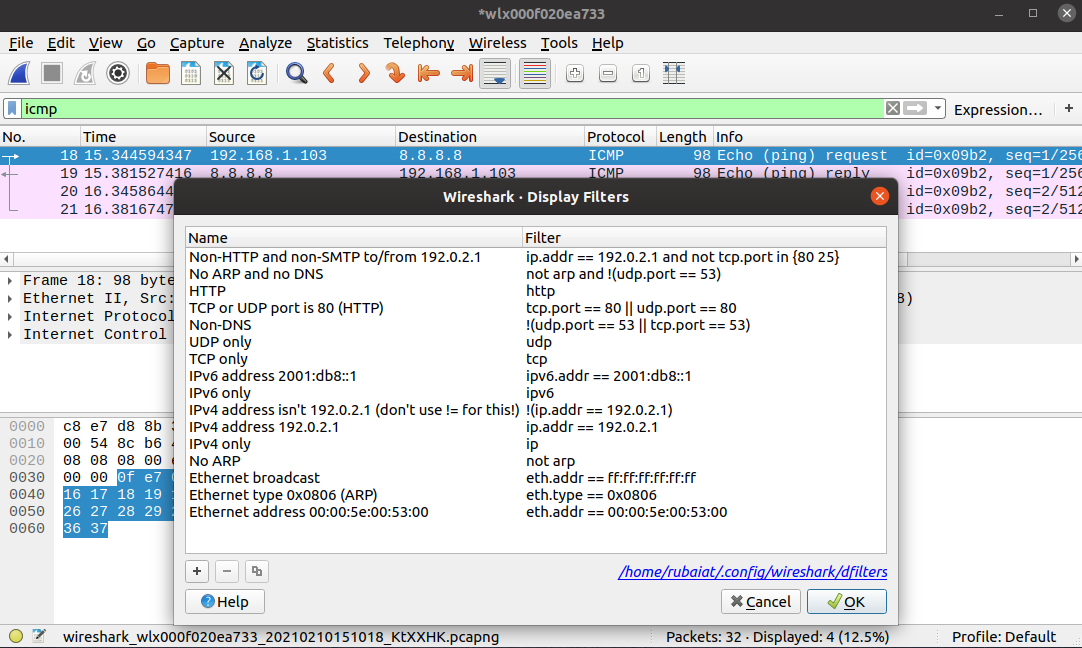
You can choose from a large number of filters. Moreover, you can also define custom filtering rules for trivial tasks. To add personalized filters, go to Analyze > Display Filters. Click on the + icon to add a new filter.
Using Wireshark Capture Filters
Capture filters are used for specifying which packets to capture during a Wireshark session. It produces significantly fewer packets than standard captures. You can use them in situations where you need specific information about certain packets.
Enter your capture filter in the field just above the interfaces list in the main window. Select the interface name from the list and type in the filter name in the above field.
Click on the blue shark fin icon to start capturing packets. The following example utilizes the arp filter to capture only ARP transactions.
Using Wireshark Coloring Rules
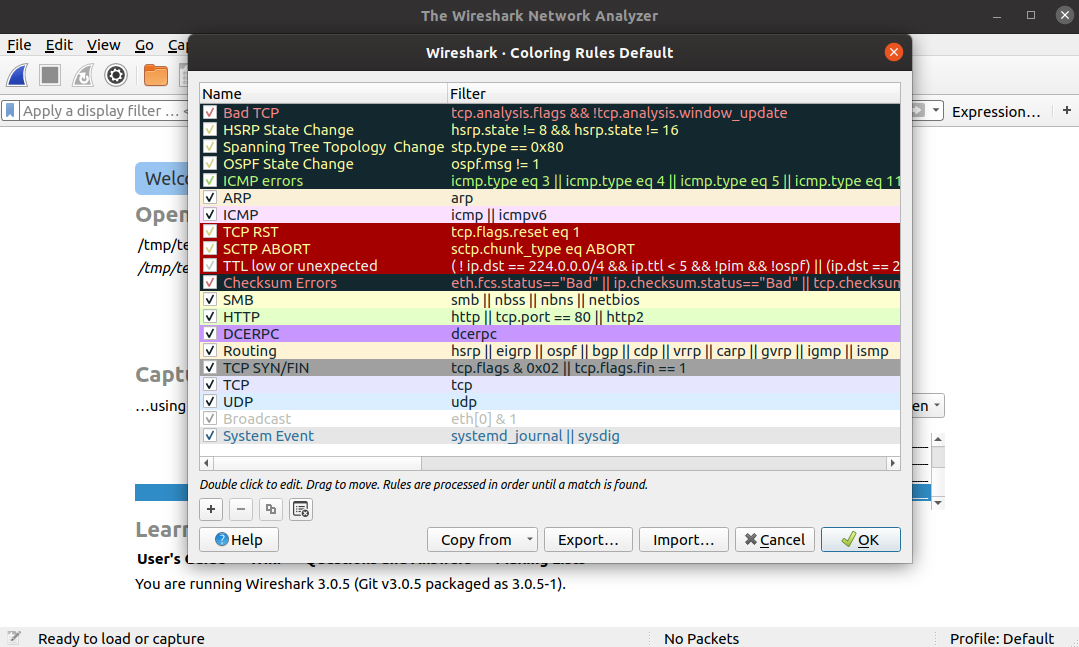
Wireshark provides several coloring rules, which were previously termed as color filters. It's a great feature to have when analyzing extensive network traffic. You can also customize them based on preference.
To display the current coloring rules, go to View > Coloring Rules. Here you can find the default coloring rules for your installation.
You can modify them any way you want. Plus, you can also use other people's coloring rules by importing the configuration file.
Download the file containing the custom rules and then import it by selecting View > Coloring Rules > Import. You can export rules similarly.
Wireshark in Action
So far, we have discussed some of Wireshark's core features. Let's perform some practical operations to demonstrate how these integrate.
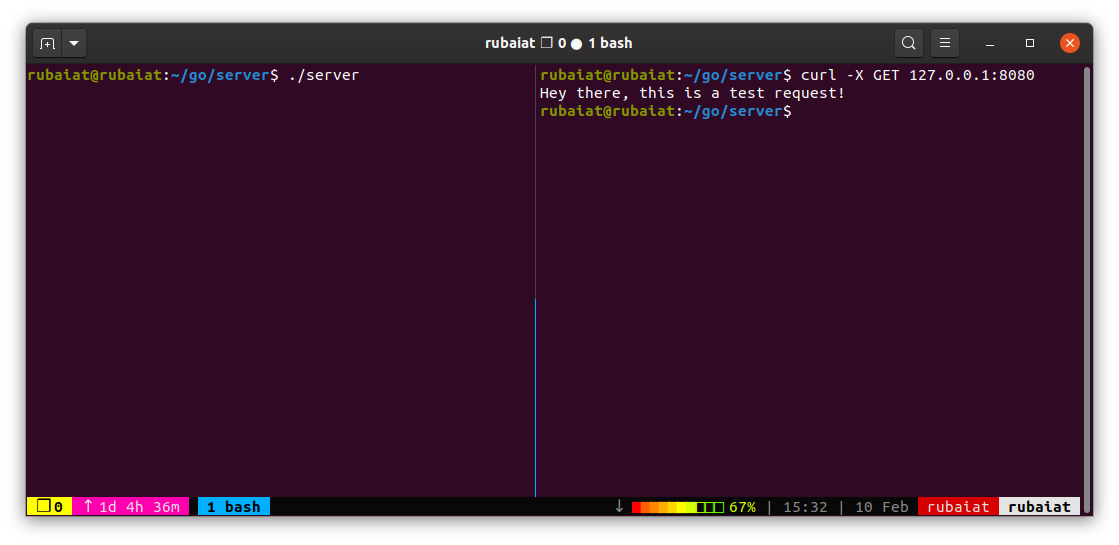
We've created a basic Go server for this demonstration. It returns a simple text message for each request. Once the server is running, we'll make some HTTP requests and capture the live traffic. Note that we're running the server on the localhost.
First, we initiate the packet capture by double-clicking on the Loopback(localhost) interface. The next step is to start our local server and send in a GET request. We're using curl to do this.
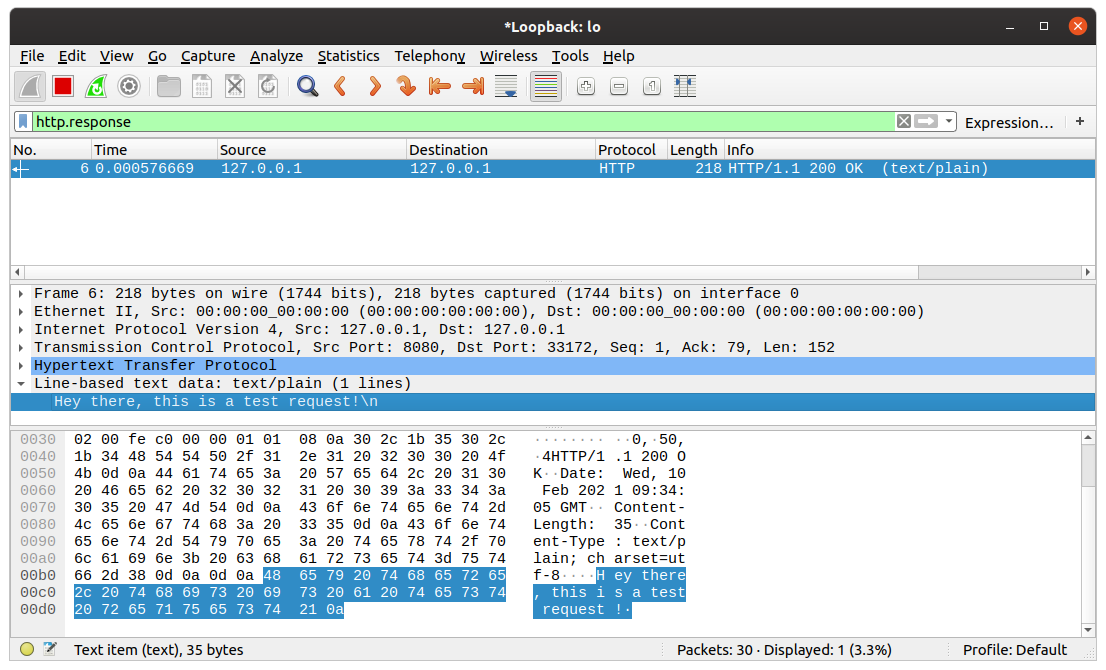
Wireshark will capture all incoming and outgoing packets during this conversation. We want to view the data sent by our server, so we'll use the http.response display filter for viewing the response packets.
Now, Wireshark will hide all other captured packets and display the response packets only. If you look closely at the packet details, you should notice the plaintext data sent by our server.
Useful Wireshark Commands
You can also use various Wireshark commands to control the software from your Linux terminal. Here are some basic Wireshark commands:
- wireshark starts Wireshark in graphical mode.
- wireshark -h displays the available command-line options.
- wireshark -i INTERFACE selects INTERFACE as the capturing interface.
Tshark is the command-line alternative for Wireshark. It supports all the essential features and is extremely efficient.
Analyze Network Security with Wireshark
Wireshark's rich feature set and advanced filtering rules make packet analysis productive and straightforward. You can use it to find all sorts of information about your network. Try out its most basic functionalities to learn how to use Wireshark for packet analysis.
Wireshark is available to download on devices running Windows, macOS, and Linux.